Sniffmap shows risks of interception, per country
Sniffmap is a project to map the potential Internet mass interception performed by NSA and its allies (USA, UK, Canada, Australia, New Zealand). Since Edward Snowden disclosure, the security space has changed: rumors have been confirmed, data points have been available and new knowledge about security exposure and attack vectors is now known. This project tries to put this in easy to grasp visual representation, within the bigger context of TelcoMap.org.
Actually, we get route data not only per country but also per ISP and operator, but for now we didn't find a way to visualize that neatly.
Results
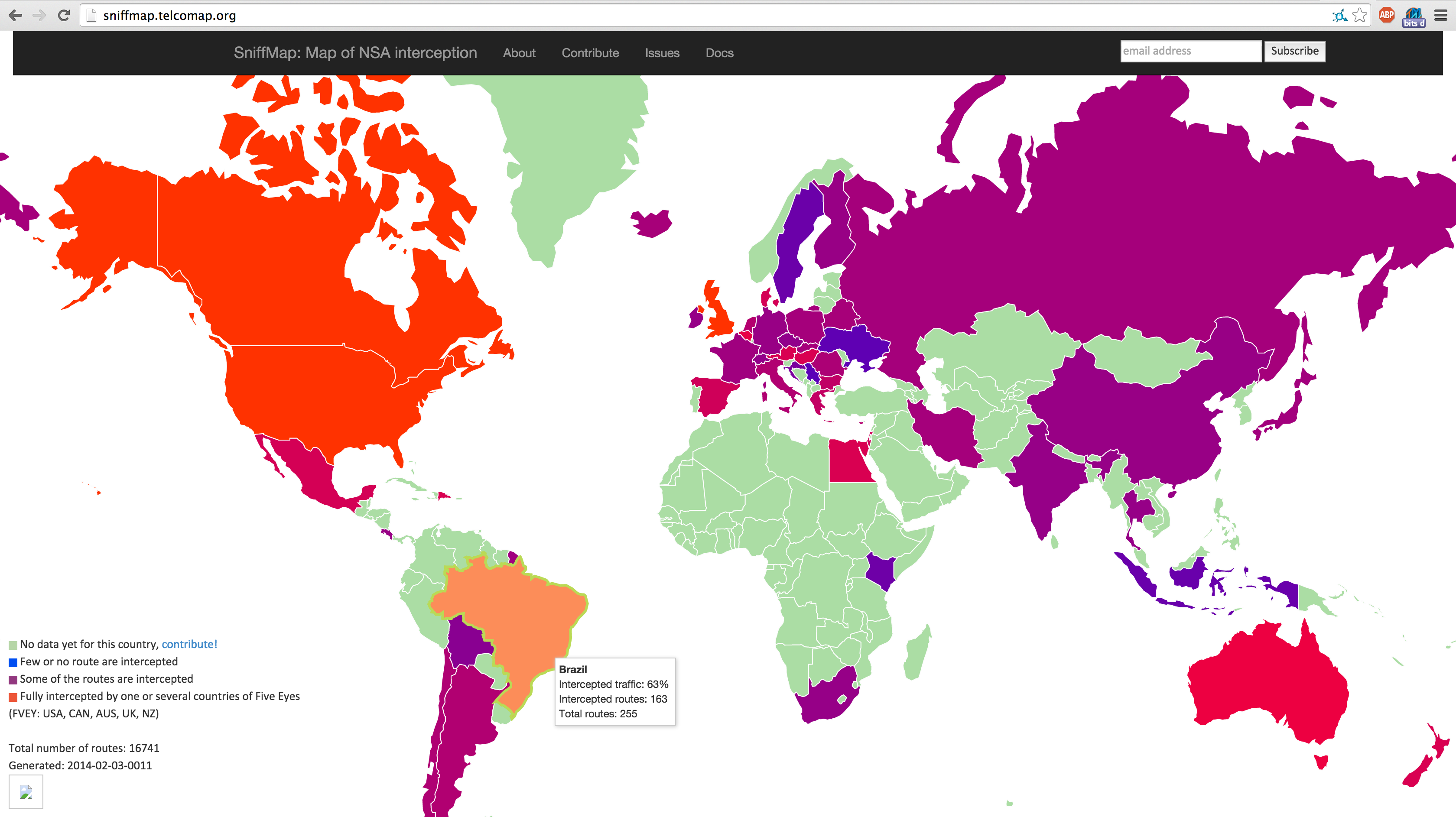
Better display: http://sniffmap.telcomap.org/
Research methodology
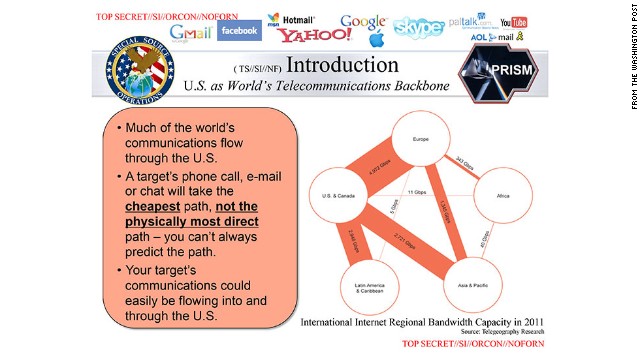
As stated in the fateful NSA document, many telecommunication links go through USA and its allies to connect two other countries. This is due to least cost routing and link usage. Therefore, NSA can leverage on this to capture a lot of traffic that otherwise would not go through its points of interception.
To create our dataset, we try to detect each time an internet route between two IP addresses pass by an NSA controlled country and therefore can be considered as intercepted. As you'll see, around 80% of the Internet is captured by NSA and allies.
Our metholody is the following
- Choose a random list of target IP address
- For each country take all known traceroute gateways
- For each traceroute gateways test each target IP address (within a pool of 255 random IP with each of the 255 class A networks)
- If this route goes through one NSA-controlled country, mark the route as "bad", otherwise the route is marked as good.
- Compute percentage over all routes for a given country (using multiple traceroute gateways hence hopefully multiple ISPs and operators to have meaningful results)
Known bias
There are a few known bias
- Results are dependent on the variety of traceroute source (i.e. traceroute http gateways, looking glass, local shell access, ...).
- Results are dependent on the fact that even if traceroute sources are varied, they should be depending of different BGP AS (Autonomous Systems) in order to really represent the country's traffic.
- This analysis is not weighted by country's traffic quantity per AS, thus it is a percentage of _routes_ potentially intercepted, not of quantity of traffic intercepted.
- Not only NSA and the "Five Eyes" allies are intercepting Internet traffic. It seems to have become a popular sport these days. So you can expect also some other countries to intercept and therefore the real stats should be much higher.
- We're depending on geographic IP lookup data tables to determine location of routers. Since these cannot be 100% accurate, our stats are biased.
- On a given route, the fact that a router is attributed to one country does not clears other routers as these could also be compromised by NSA and allies or even owned by a collaborating company.
- The routes shown by traceroute may not show the underlying physical nor layer 2 network topology, such as MPLS, satellite links or fiber optic (DWDM or else) network. Therefore, this is another risk of interception and another set of location for such interceptions.
- If a router from a non-NSA controlled country was compromised (and backdoored) by NSA to establish mass-intercept, they would probably pay attention that this attack remain "non attribuable". Non-attribution is a critical criteria of cyber security. That would mean using countries which would probably not be within Five Eyes and certainly not within USA. This would cause a false negative that is extremely hard to detect: hard to the point it is designed to be concealed even to local counter-intelligence services of the targeted country.
- Highly dysfunctionnal national Internet backbones and ISPs will make appear a country as less intercepted. It's in reality not because they are not intercepted but because many routes fail to reach their target. We should add reachability testing of known reachable destinations, yet many of our traceroute sources do not support this kind of test. It would restrict the number of results for the sake of better integrity checking. To fix this, we prefer to focus on having more collaborators provide us with endpoints locations enabling us on this.
BGP
Ok, so this research deals with routes, so why not using BGP? Well, there are many reasons why we don't use BGP for conducting this analysis:
- BGP is just an information store, a distributed route database. It does not imply that the routes described in BGP tables are going to be the routes used by all routers on the path. So this means that it could introduce a measurement bias.
- In the case that NSA and allies would backdoor third party routers to conduct interception, they would take good care to not alter the BGP tables so that the traffic redirect wouldn't be observable outside of the compromised infrastructure.
- Some routers which direct packets before it reaches the Internet BGP routers may be statically configured to use specific other links than the one dictated by the country. This would not show up in BGP tables yet provide alternate routes to some selected customers.
Contribute!
As you can see, many countries do not have measurement yet. You can help improve this by providing us traceroute results. To do this, simply run the following command (preferrably from machines located within these countries without any data yet.):
$ curl http://sniffmap.telcomap.org/netprobe.php | bash
$ curl http://sniffmap.telcomap.org/netprobe.php?debug=1 | bash
This will run traceroute (or even mtr if it is installed) and report result to SniffMap.
Traceroute for bitcoins
Bitcoin millionaire, or just happy passionates, you can contribute to this effort: you are wealthy, and not living in one of these countries where we don't have data. But you can still help! You can donate Bitcoins (and other cryptocurrencies), this will become bounty for contributors. We will then redistribute bitcoins to the ones who contribute traceroute data. Donate any amount you wish, mountains are made of atoms.
Send us bounty:- Bitcoin: 132HbTVNrGWF15EVuatUgoocMFtWE1Hz1F
- Anoncoin: AJGo5KNNKnD3E4obhB6ms3313UrAyPN6xH
- Ripple: rs3cYkNHqHhKLEvdbfhvrQMAo2CBtXxBZx
We will also try to rent VMs in countries we need for route diversity and SniffMap analysis.
Receive bounty:
Contribute gateways or traceroute submissions, send us a cryptocurrency address, and we'll redistribute bounty to you! Please communicate your crypto currency address along with your contributed data (source IP or shell account, etc...)
Join!
We are definitely looking for people who can help on the coding and on the deployment side of SniffMap. If you want to chat about that, you can join freenode's #tmplab and ask around or send us a mail. Also, have a look on Issues, if you want to help: https://github.com/P1sec/sniffmap/issuesGet notified
People
This research has received contributions such as raw materials, inspiration and collaboration from:
- P1 Security's P1 Lab project telcomap.org
- /tmp/lab hackerspace
- Alban Crommmer from /tmp/lab and La Quadrature du Net; specifically for his help and his inspiring work NSA Observer
- Antoine Mazière's research on networks such as http://porngram.sexualitics.org/
- Tetaneutral
- These security map research (SniffMap and others) will be presented at a workshop during Hackito Ergo Sum 2014 in Paris, come to this great conference and let's share a beer there.
- Marc Bruyere network support and ideas
- Renaud S. on maps